
What’s new with Microsoft in open-source and Kubernetes at KubeCon North America 2025
From improving reliability and performance to advancing security and AI-native workloads, our goal remains the same: make Kubernetes better for everyone.
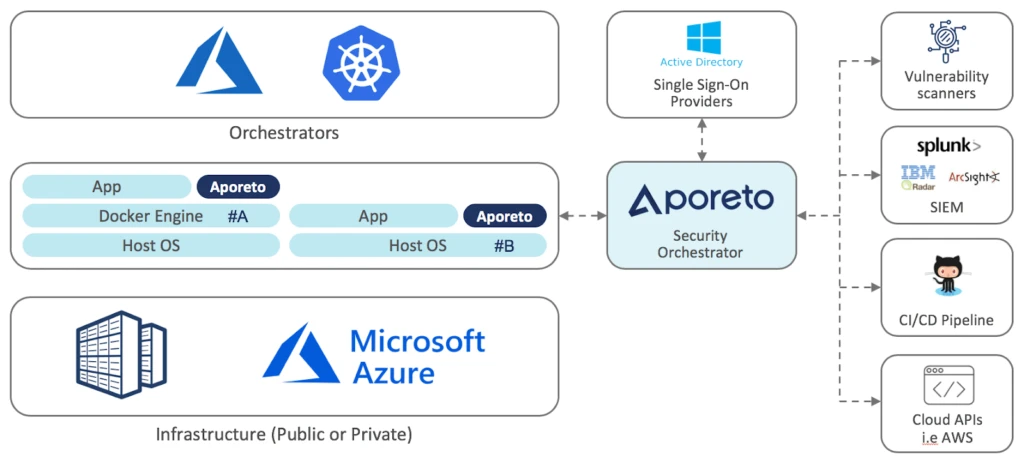
Azure Kubernetes Service (AKS) makes it simple to deploy a managed Kubernetes cluster in Azure. AKS reduces the complexity and operational overhead of managing Kubernetes by offloading much of that responsibility to Azure and handling critical tasks like health monitoring and maintenance. However, your operational needs may require you to deploy your Kubernetes cluster in a hybrid setting. For instance, your data services may be running in your private cloud while application logic services could be running in AKS.
Without the proper toolset and configuration, maintaining visibility and security for your distributed environment can be hard to configure and maintain. In this blog, we focus on providing centralized visibility and monitoring for these types of distributed workloads in a manner that is easy to deploy and manage. By following step 5 in the blog below, you will learn how to easily enforce network and service layer access policies in your AKS cluster with Aporeto. You may extend these policies in a hybrid environment without any network configuration or code modification.
Aporeto is a Zero Trust security solution for microservices, containers and cloud. Fundamental to Aporeto’s approach is the principle that everything in an application is accessible to everyone and could be compromised at any time. Aporeto uses vulnerability data, identity context, threat monitoring and behavior analysis to build and enforce authentication, authorization and encryption policies for applications. With Aporeto, enterprises implement a uniform security policy decoupled from the underlying infrastructure, enabling workload isolation, API access control and application identity management across public, private or hybrid cloud.
Because Aporeto transparently binds to application components to provide them with identity, the result is security independent from infrastructure and network and reduction of complexity at any scale on any cloud.

You can visualize the application of your choice by deploying Aporeto as an AKS DaemonSet (see #A in diagram above). If you control the virtual machines on which your application component run, you may also deploy Aporeto as a Docker container or a userland process (see #B in diagram above).
Aporeto auto-generates application security policy by ingesting Kubernetes Network Policies and RBAC. You also have the option of leveraging your application dependency graph that Aporeto creates to describe the application’s behavioral intent as policies. In every case, you may audit and edit auto-generated policies and inject human wisdom when necessary.
Once you have policies, you may simulate their enforcement at runtime to evaluate the effects of your security policies without interrupting operations. When satisfied that your security policies are solid, you may lockdown your application and protected it with a Zero Trust approach.
Because Aporeto untethers application security from the network and infrastructure, one key benefit of Aporeto’s approach for protecting your containers, microservices and cloud applications is that you can have a consistent security approach even in a hybrid or multi-cloud setting. As you gain experience with Aporeto in a single cluster setting, you will quickly realize how easy it is to have a consistent security posture in multi-cluster and multi-cloud settings without any infrastructure or operational complexity.
You will need the following binaries installed in your path.
Using a browser login select the desired namespace where the cluster will be placed. The select and expand “System” and then select “Kubernetes Clusters”. Click on the “+” icon (top right). Give the cluster the name “aks1” and leave all defaults as they are. Click on create. This will create the cluster and cause a file with the name aks1.tar.gz (assuming you named the cluster aks1) to be downloaded to your browser download directory. Take note of this file as we will need it later.
If you have not already done so, log into Azure with the following Powershell or Bash commands:
az login
Then create a working directory with the following Powershell or Bash commands:
mkdir -p aks; cd aks
Move the file downloaded in the previous step into the working directory.
Create the Kubernetes cluster on AKS with the following Powershell or Bash commands.
az group create --name aporeto_lab --location eastus
az aks create --resource-group aporeto_lab --name aks1 --node-count 2 --generate-ssh-keys
az aks get-credentials --resource-group aporeto_lab --name aks1 -f kube.cfg
Set the kubectl config file in the environment.
With PowerShell
$loc = Get-Location Set-Variable -Name “KUBECONFIG” -Value “$loc/kube.cfg”
With Bash
export KUBECONFIG=$PWD/kube.cfg
and then verify that the nodes are operational with the following Powershell or Bash commands:
kubectl --kubeconfig kube.cfg get nodes
you should see something like this:
->kubectl get nodes
NAME STATUS ROLES AGE VERSION
aks-nodepool1-82983338-0 Ready agent 3m v1.9.6
aks-nodepool1-82983338-1 Ready agent 3m v1.9.6
Extract the contents of the file aks1.tar.gz and create the kubernetes resources with the bash commands (or Powershell equivalent. This may require a utility such as 7zip).
mkdir -p kube_aporeto
tar xfv aks1.tar.gz -C kube_aporeto
kubectl create -f kube_aporeto
then check the status with the command:
kubectl get pods -n kube-system
you should see something like:
->kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
aporeto-enforcer-fkf46 1/1 Running 0 23s
aporeto-enforcer-v4k5r 1/1 Running 0 23s
aporeto-kubesquall-h4m5d 1/1 Running 0 21s
azureproxy-79c5db744-t2654 1/1 Running 2 4m
heapster-55f855b47-drbb2 2/2 Running 0 3m
kube-dns-v20-7c556f89c5-mcg6z 3/3 Running 0 4m
kube-dns-v20-7c556f89c5-xhts7 3/3 Running 0 4m
kube-proxy-h5rqq 1/1 Running 0 4m
kube-proxy-s7rkq 1/1 Running 0 4m
kube-svc-redirect-92tvv 1/1 Running 0 4m
kube-svc-redirect-h2dmp 1/1 Running 0 4m
kubernetes-dashboard-546f987686-7gzln 1/1 Running 2 4m
tunnelfront-66fd996c74-dlpdm 1/1 Running 0 4m
Clone the github repo https://github.com/aporeto-inc/apowine.git and then follow the instructions in the README.md file. By following this tutorial, you will learn how to enforce network and service layer access policies in your AKS cluster.
Now that you have connected your AKS Kubernetes cluster to Aporeto, you can visualize it in real time and on historical bases using the Aporeto UI. You can also connect your private cloud workload to your Aporeto account and view your distributed application’s end-to-end operations centrally.
You can find instructions for connecting non-AKS workloads to Aporeto by perusing the document (click on “Switch to Accounts” (top right corner user icon, immediate right of the “?” mark icon). As always, you can request support directly in Aporeto’s Console or via this link.
Aporeto’s powerful security capabilities unlock the following use cases, among others:
To learn more, please visit https://www.aporeto.com/demo/
Enjoy!
The Aporeto Team